Exploring Denial-of-service (Dos) Attacks In Ethical Hacking
- - Category: Online Education
- - 13 Dec, 2023
- - Views: 10
- Save
ACTE, a renowned provider of training, specializes in delivering comprehensive Training courses.
In the realm of ethical hacking, understanding the concept of a denial-of-service (DoS) attack is crucial. A DoS attack involves the intentional disruption of a network, system, or application’s normal operation by overwhelming it with a flood of illegitimate requests or excessive traffic.
We will delve into the fundamentals of DoS attacks in ethical hacking and their role in security assessments.
Let’s dive deeper into some of the best ones, with a particular highlight on the unique certified ethical hacker course in Bangalore

Understanding DoS Attacks:
A DoS attack is a technique employed by ethical hackers to assess the resilience and vulnerability of a network or system against malicious attempts to disrupt its services. By simulating a DoS attack, ethical hackers can help organizations identify weaknesses and develop effective mitigation strategies to safeguard against real-world attacks.
Types of DoS Attacks:
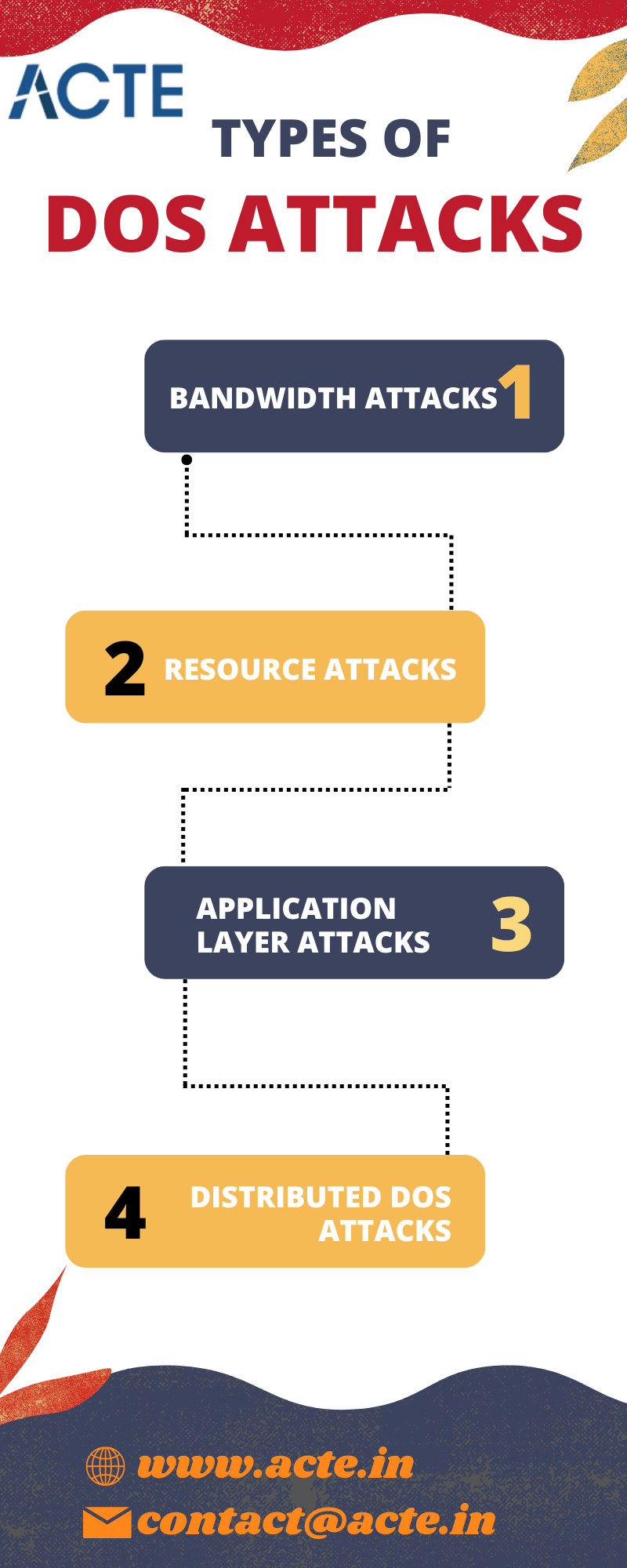
- Bandwidth Attacks:
Bandwidth-based DoS attacks aim to consume the target’s network resources by flooding it with an overwhelming volume of traffic. By utilizing techniques like UDP flooding, ICMP flooding, or SYN flooding, attackers inundate the network, rendering it inaccessible to legitimate users. - Resource Attacks:
Resource-based DoS attacks focus on depleting the target’s system resources, such as CPU, memory, or disk space. By exploiting vulnerabilities or design flaws, attackers consume resources excessively, causing system slowdown or unresponsiveness. - Application Layer Attacks:
Application layer DoS attacks specifically target the application or web server, exploiting weaknesses in the application code or server configuration. Attackers inundate the application or server with a large number of complex requests that require extensive processing, leading to unresponsiveness or system crashes. - Distributed Denial-of-Service (DDoS) Attacks:
DDoS attacks involve multiple compromised devices forming a botnet or network of attacker-controlled machines. Attackers coordinate these devices to simultaneously flood the target network or application with a massive volume of traffic. This makes it challenging to distinguish legitimate requests from malicious ones, causing service disruption.
Ethical Considerations:
Ethical hackers conducting DoS attacks adhere to responsible and controlled methodologies to ensure no permanent damage or disruption occurs. The objective is to identify vulnerabilities and weaknesses, helping organizations enhance their defenses against such attacks.
However, it is essential to note that engaging in DoS attacks without proper authorization is illegal and unethical. Ethical hackers must always obtain explicit permissions and adhere to legal and ethical boundaries when performing security assessments or penetration testing.
Mitigation and Defense:
To defend against DoS attacks, organizations can implement several strategies, including:
- Load Balancers: Distribute incoming traffic across multiple servers, reducing the impact of a DoS attack by sharing the load.
- Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS solutions to detect and mitigate DoS attacks in real-time by identifying abnormal traffic patterns.
- Rate Limiting: Implement rate-limiting mechanisms to restrict the number of requests from a single source, preventing overwhelming traffic.
- Traffic Filtering: Utilize network filtering techniques to block or filter malicious traffic originating from known attack sources.
Denial-of-Service (DoS) attacks play a vital role in ethical hacking as they help organizations understand the vulnerabilities and weaknesses in their networks and systems.
By simulating DoS attacks, ethical hackers provide valuable insights that enable organizations to fortify their defenses and protect against real-world threats. However, ethical hackers must always operate within the boundaries of legality and ethics, obtaining proper authorization and adhering to responsible methodologies when conducting DoS attack simulations.
To learn more considering a top ethical hacking training institute can provide certifications, job opportunities, and experienced guidance, available both online and offline. Experienced teachers can help you learn better. Take it step by step and consider enrolling for a better understanding.
If you feel that my response has been helpful, to encourage me to upload more content about digital marketing. Thank you for spending your valuable time and upvotes here. Have a great day!


